Privacy law in practice: Lessons from the OAIC’s latest data breach report
The release of the Office of the Australian Information Commissioner's (OAIC) latest Notifiable Data Breaches Report offers valuable insights into emerging privacy risks and regulatory expectations and serves as a timely reminder during Privacy Awareness Week (16 – 22 June) of the importance of robust data protection practices.
On 13 May 2025, the OAIC released its latest Notifiable Data Breaches Report, summarising notifications received between 1 July and 31 December 2024 under the Notifiable Data Breaches (NDB) scheme.
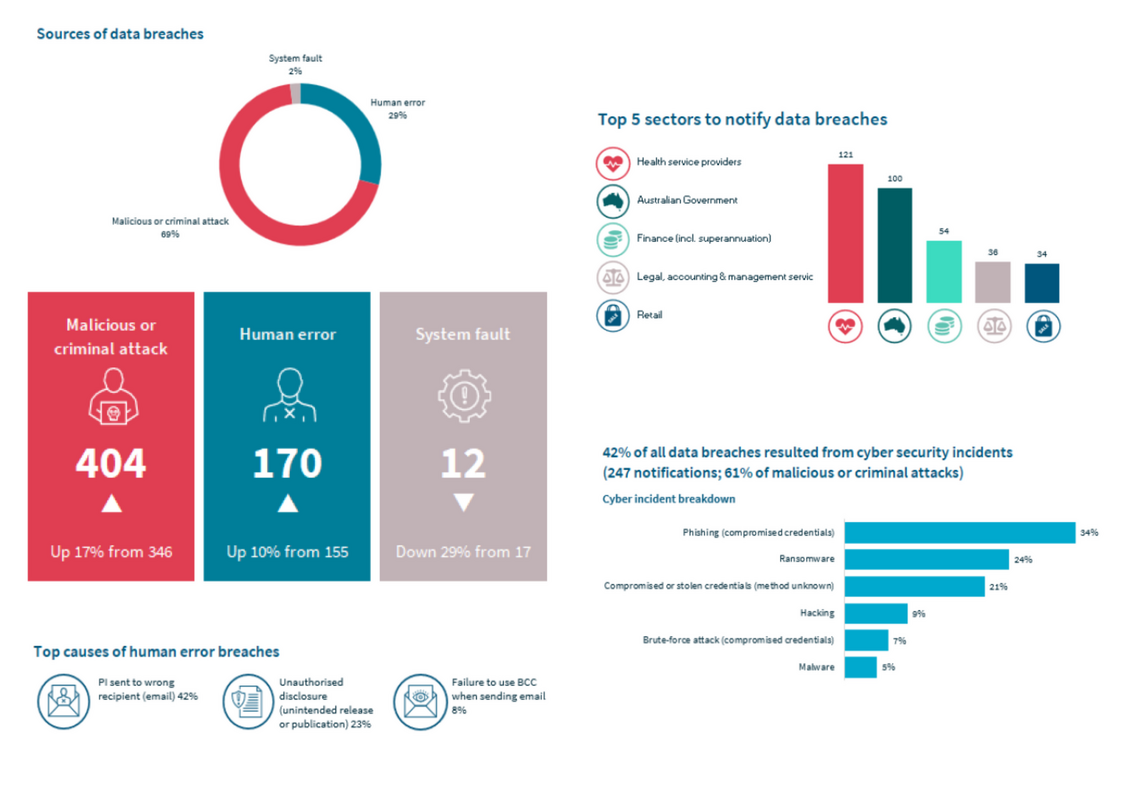
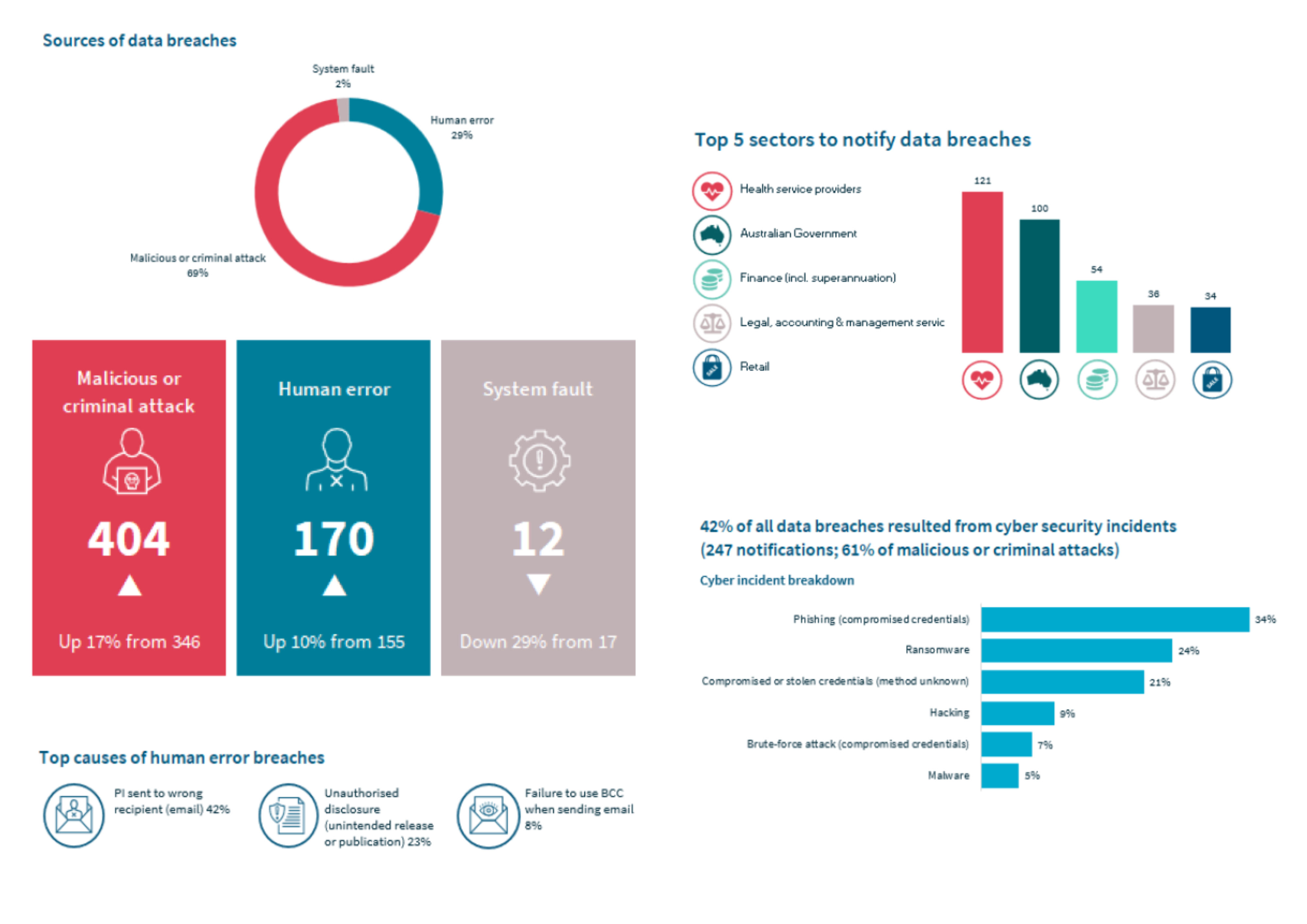
According to the OAIC, 2024 recorded the highest annual volume of breach notifications since the NDB scheme commenced in 2018. This reflects both the persistent challenges to information security and the growing maturity of breach detection and reporting practices across Australian organisations.
The report depicts a threat landscape still dominated by external attacks, though preventable internal errors remain prevalent.
- Malicious or criminal attacks accounted for 69% of all notifications.
- Of these, cyber security incidents comprised 61%, followed by social engineering and impersonation (28%) (which involves manipulating individuals into bypassing security protocols, such as through invoice fraud). Social engineering and impersonation was particularly prevalent in breaches reported by the Australian Government.
- Phishing (34%) was the most reported cyber incident, followed by ransomware (24%) and stolen or compromised credentials (20%).
- Human error contributed to 29% of data breaches, with the disclosure of personal information via email to the wrong recipient accounting for 42% of human error breaches.
Implications for organisations
For organisations regulated under the Privacy Act 1988 (Cth), the report highlights several areas for targeted risk and compliance activity.
Under Australian Privacy Principle (APP) 11, organisations must take reasonable steps to protect personal information (PI) they hold from misuse, interference, loss, unauthorised access, modification or disclosure.
Recent amendments to APP 11 clarify that “reasonable steps” extend to both:
- technical measures (eg encryption, multi-factor authentication); and
- organisational measures (eg privacy training, data handling policies, and incident response protocols).
The frequency of breaches arising from phishing, impersonation and misdirected emails reinforces the continuing role of human error in data incidents. As such, regular privacy and cyber security awareness training for all personnel (including staff and contractors) remains a vital control.
Similarly, the prevalence of breaches involving compromised credentials signals the need for multi‑factor authentication, particularly for externally accessible or sensitive systems, supported by strong password management and access control policies.
The OAIC also reiterates that the duty to notify begins when any employee becomes aware of an incident underlying a notifiable data breach, not when it reaches legal, security or executive teams.
To meet these obligations, organisations should ensure that their incident response plans are not only robust and documented, but also well-communicated and understood across the business. Regular vulnerability assessments and security assurance testing are also essential.
For further insight into regulatory expectations regarding the steps organisations should take to protect personal and sensitive information from misuse, interference or unauthorised access, see:
- the OAIC’s concise statement in its civil penalty proceedings against Medibank (here);
- the OAIC’s acceptance of an enforceable undertaking from Oxfam Australia (here); and
- ASIC’s concise statement in its civil penalty proceedings against FIIG Securities Limited (here).
With the OAIC’s enhanced enforcement powers, higher penalties and the proposed Tranche 2 Privacy Act reforms, organisations should ensure their privacy and cyber frameworks are not only compliant, but capable of withstanding greater scrutiny and increased enforcement action.
Images from OAIC - Notifiable data breach report - July to December 2024
This article provides general commentary only. It is not legal advice. Before acting on the basis of any material contained in this article, seek professional advice.
Related Insights
Don’t leave your business exposed when conducting cyber incident investigations

Invoice fraud: Who pays when scammers strike?

Deep Dive into Privacy Act Reforms

Cyber Security Bill 2024 – be alert, not alarmed


